Screenshots
Screenshots
Opinions from Deniece Watkins Smith, Realtor, ePro, SRES. News, laws, information regarding current real estate issues.
20 Best Free hacking apps For Android |2019|.
Android is now one of the most popular operating systems. So, hackers have also started using Android devices for their tasks. Now Android devices are used for penetration testing and other hacking activities including IT security administrator, Wi-Fi hacking and network monitoring. There are several hacking apps or Android devices. So, we have curated a list of best hacking apps for Android.
Before you start using these apps, you must take a backup of your important data. I also recommend the use of these apps on a separate device. Using this on your primary phone is not recommended. It is because many of these apps require a rooted device and app can also harm your phone.
Note: Hacking apps can be used for educational and malicious purpose. But we never encourage malicious operations. We are listing the apps here just for educational purpose. You should only use these apps to learn. We do not support any unethical use of these apps.
AndroRAT stands for Android RAT. RAT is the short form of Remote Administrative Tool and it allows an attacker to remotely control and fetch information from a device. AndroRAT does the same thing. It has a server developed in Java/Swing but the Android application has been developed in Java Android.
AndroRAT allows you to connect information like call logs, contacts, messages, location and more. You can remotely monitor sent and received messages send texts, use the camera, open a URL in the browser, make phone calls and remotely monitor the device.
The connection to the server can be triggered by an SMS or a call. From the server GUI, you can check all the connected clients and access information.
As the app allows silent remote access, it is not available on Play Store.
zANTI is a known penetration testing suite of applications you can install locally on Android smartphone. This tool brings scanning tools Diagnostic features and Reporting tools. You can use this malicious software to attack a network and check for any loopholes in your network. This tool is used to test redirect and SSL stripping attacks. You can edit request and response messages from web servers, the host takes websites from your Android phone and more.
FaceNiff is another good Android hacking that allows you to intercept the traffic of your WiFi network. You can use this tool to snoop what people are doing on the network you are. You can snoop on services like Facebook, Twitter, Amazon, YouTube and more. This is one of the notable too for steal cookies from the WiFi network and gives the attacker unauthorized access to other people's account.
This app requires a rooted device. So, you can only use the app if you have a rooted phone.
Droidsheep is also a similar app that helps security analysts understand what is happening in your Wi-Fi network. Like Face Sniff, this app can also hijack the web session profiles over a network and supports most of the services and websites.
The primary difference between Droidsheep and FaceSniff is that Droidsheep works with almost all the websites while FaceSniff has limited support.
Hackode is another good hacking apps for Android. It is not a single app but a collection of tools for ethical hackers and penetration testers. The app comes with three modules including Reconnaissance, Scanning and Security Feed. You can use this app for SQL Injection, Google hacking, MySQL Server, Whois, Scanning, DNS Dif, DNS lookup, IP, MX Records, Security RSS Feed, Exploits etc.
The app is still in beta, but available in Play Store.
cSploit is also a good security tool for Android. It comes with several options like cracking Wi-Fi password, installing backdoors, finding vulnerabilities and their exploits. If you are looking for a good hacking app or hacker app for Android, you should try this one for sure.
DroidBox is also a similar kind of app that allows you to do the dynamic analysis of Android applications. You can use this app to get information like hashes of APK package, network traffic, SMS & phone calls, Incoming/outgoing network data, Listing broadcast receivers and more.
If you are into security or hacking, I am sure you already know the name of this too. Like the desktop tool, Nmap for Android also allows you to scan
It works on both on non-rooted and rooted phones. If you are a beginner, you should try this app and learn from it.
SSHDroid is SSH tool developed for Android. It lets you connect to a remote computer and run terminal commands, transfer and edit files. The app also provided features like shared-key authentication, WiFi autostart whitelist, extended notification control etc,
This app is available on Play Store.
Kali Linux NetHunter is an open source penetration testing platform for Android. It officially supports Nexus and OnePlus devices. It provides the ultimate penetration testing platform that allows you to perform a wide range of attacks.
APKInspector allows you to perform reverse engineering on an APK. you can use this to get a deep insight or APK and get the source code of any Android app. You can do modifications in the APK and visualize the DEX code to erase the credits and license.
Shark for Root is an advanced hacking tool for security experts and hackers. It can work as a traffic snipper. You can use the tcpdump command on rooted devices. It works on Wi-Fi, 3G, and FroYo tethered mode.
dSploit is an Android network penetrating testing suit. You can download and install it on your device to perform network security testing. It supports all Android devices running on Android 2.3 Gingerbread or higher. You need to root this phone for using the app. After rooting the phone, you need to download BusyBox from Google Play Store
The app comes with several modules including Port Scanner, Inspector, RouterPWN, Trace, Login Cracker, Packet Forger, Vulnerability Finder, and MITM.
WPScan is a WordPress vulnerability scanner for Android. This app is used to scan WordPress based websites and find possible vulnerabilities. WPScan is a popular desktop tool but this WPScan for Android is not related to that. So, do not think of it as an official WPScan app.
Network Mapper is a network scanner tool for network admins. It used to scan the network, lists all devices connected and find Open ports of various servers like FTP servers, SSH servers, SMB servers etc on the network. The tool is available on Play Store.
Andosid is like LOIC for the desktop. This tool is used to perform DOS attacks from Android mobile phones. You can use this tool to set a target URL and perform a DOS attack in one click. The tool will start flooding target URL with fake requests.
DroidSQLi app allows attackers to perform SQL Injection on a target URL. You just need to find a target URL and this tool will start the fully automated SQL Injection attack.
AppUse is a Virtual Machine developed by AppSec Labs. It is a freely available mobile application security testing platform that comes with lots of custom made tools by AppSec Labs. If you want to sue your Android phone as your penetration testing tool, this one is for you.
Network Spoofer is also a good hacking app for android. It lets you change the website on other people's computer from your Android phone. Connect to a WiFI network and then choose a spoof to use with the app. this tool is to demonstrate how vulnerable a network is. Do not try this on any unauthorized networks.
As the name suggests, DroidSheep Guard works against DroidSheep. It monitors Android devices' ARP-table and tries to detect ARP-Spoofing attack on your network. It does not require a rooted device.
@EVERYTHING NT
 Research: Dr. Web. Linux.Lady
Research: Dr. Web. Linux.Lady
 |
| Test suite for analyzing PayPal's API [1] |
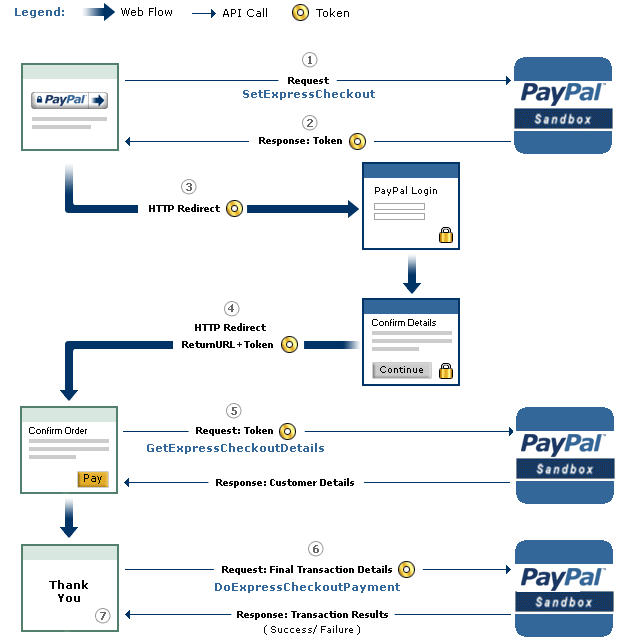 | ||||
| PayPal's Express Checkout [2] |
 |
| Magento can raise the authorized amount and debit more money from the user's account |
Type: ifconfig wlan0 (if you are using WiFi)
Type: ifconfig eth0 (if you are using eth0)
Type: ifconfig (It display all information about your network)
